2.1 WinDbg 的使用
WinDbg 無疑是 Windows 下進行漏洞分析的首選工具,較之 OD、IDA 等調(diào)試器,作為微軟內(nèi)部開發(fā)的 WinDbg 其優(yōu)勢還是很明顯的。它同時支持 ring3 層和 ring0 層的漏洞調(diào)試,特別是 ring0 層下,目前還沒有哪個調(diào)試器能夠與其相媲美。WinDbg 于 Windows 就好像 GDB 之于 Linux,固漏洞分析人員掌握其使用方法還是很有必要的,本部分內(nèi)容將主要介紹 ring3 層和 ring0 層下 WinDbg 的一些常見命令及使用技巧。
**初識 WinDbg**
WinDbg 界面中包含多個子窗口,如命令窗口、寄存器窗口、內(nèi)存窗口、反匯編窗口等,其中最重要的是命令窗口,其余子窗口顯示的內(nèi)容實際上都可以通過特定的命令來得到,可以說命令調(diào)試是 WinDbg 的精髓所在。
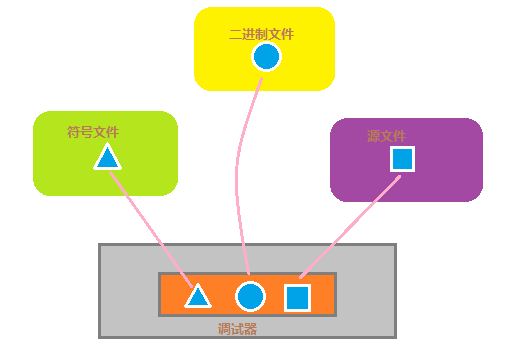
在安裝完 WinDbg 后,我們要為其配置調(diào)試符號信息,即微軟提供的 pdb 文件,除了可以通過符號服務(wù)器實時獲取外,還可以到官網(wǎng)下載獨立的符號文件安裝包。當(dāng)然,其它軟件開發(fā)商可能也會提供符號信息,可以根據(jù)具體分析需求來進行設(shè)置。對程序調(diào)試而言有源文件自然是最好的,如果沒有,能提供符號文件那么對漏洞的分析調(diào)試也會有莫大的幫助。當(dāng)然,并非所有調(diào)試程序都有符號文件,比如飽受詬病的 Office 應(yīng)用,這個時候就只能啃那些晦澀的匯編了。
我們還可以借助 WinDbg 分析藍屏 dump 文件、調(diào)試含源文件的程序等,此外,自定義插件的編寫也是支持的??偟膩碚f,WinDbg 還是很強大的。
**ring3 常見命令及使用技巧**
要學(xué)習(xí) WinDbg 的命令,首先得了解調(diào)試命令有哪些,這里面分為 3 種,即基本命令(無前綴)、元命令(前綴 “.”)和擴展命令(前綴 “!”),可分別通過`?`、`.help`和`!擴展模塊名.help`命令來查看。其中,擴展模塊名稱可通過`version`或`.chain`命令查看,分析人員也可以編寫自己的擴展模塊(插件)。雖然這些命令看起來比較多,但調(diào)試過程中常用的命令其實并不多,關(guān)鍵靠平時積累。執(zhí)行完前面的命令,界面可能比較亂了,先清下屏`.cls`。接著我們就來詳細看下:
- 列舉調(diào)試的進線程狀態(tài),前面的小點表示當(dāng)前進程或線程。
```
0:004> |
. 0 id: 135c create name: notepad.exe
0:004> ~
0 Id: 135c.ac4 Suspend: 1 Teb: 00000077`58a19000 Unfrozen
1 Id: 135c.eb0 Suspend: 1 Teb: 00000077`58a1b000 Unfrozen
2 Id: 135c.13b0 Suspend: 1 Teb: 00000077`58a1d000 Unfrozen
3 Id: 135c.810 Suspend: 1 Teb: 00000077`58a1f000 Unfrozen
4 Id: 135c.6b4 Suspend: 1 Teb: 00000077`58a21000 Unfrozen
5 Id: 135c.a58 Suspend: 1 Teb: 00000077`58a23000 Unfrozen
6 Id: 135c.448 Suspend: 1 Teb: 00000077`58a25000 Unfrozen
. 7 Id: 135c.102c Suspend: 1 Teb: 00000077`58a2f000 Unfrozen
9 Id: 135c.a18 Suspend: 1 Teb: 00000077`58a2b000 Unfrozen
```
- 查看進程空間的信息。
```
0:005> !address
Mapping file section regions...
Mapping module regions...
Mapping PEB regions...
Mapping TEB and stack regions...
Mapping heap regions...
Mapping page heap regions...
Mapping other regions...
Mapping stack trace database regions...
Mapping activation context regions...
BaseAddress EndAddress+1 RegionSize Type State Protect Usage
--------------------------------------------------------------------------------------------------------------------------
+ 0`00000000 0`7ffe0000 0`7ffe0000 MEM_FREE PAGE_NOACCESS Free
+ 0`7ffe0000 0`7ffe1000 0`00001000 MEM_PRIVATE MEM_COMMIT PAGE_READONLY Other [User Shared Data]
0`7ffe1000 0`7fff0000 0`0000f000 MEM_PRIVATE MEM_RESERVE <unknown>
+ 0`7fff0000 b7`26350000 b6`a6360000 MEM_FREE PAGE_NOACCESS Free
+ b7`26350000 b7`263bc000 0`0006c000 MEM_PRIVATE MEM_RESERVE Stack [~0; 1534.8dc]
b7`263bc000 b7`263bf000 0`00003000 MEM_PRIVATE MEM_COMMIT PAGE_READWRITE|PAGE_GUARD Stack [~0; 1534.8dc]
b7`263bf000 b7`263d0000 0`00011000 MEM_PRIVATE MEM_COMMIT PAGE_READWRITE Stack [~0; 1534.8dc]
+ b7`263d0000 b7`26400000 0`00030000 MEM_FREE PAGE_NOACCESS Free
+ b7`26400000 b7`265f3000 0`001f3000 MEM_PRIVATE MEM_RESERVE <unknown>
b7`265f3000 b7`265f4000 0`00001000 MEM_PRIVATE MEM_COMMIT PAGE_READWRITE PEB [1534]
...
```
- 設(shè)置特定模塊加載時中斷程序,完成操作后記得置回默認值。
```
0:000> sxe ld KERNELBASE
0:000> g
ModLoad: 00007ffc`b10b0000 00007ffc`b12cd000 C:/Windows/System32/KERNELBASE.dll
ntdll!NtMapViewOfSection+0x14:
00007ffc`b3e55354 c3 ret
0:000> sxr
sx state reset to defaults
```
- 查看進程模塊的信息。
```
0:005> lmvm KERNELBASE
Browse full module list
start end module name
00007ffc`b10b0000 00007ffc`b12cd000 KERNELBASE (pdb symbols) c:/symbols/kernelbase.pdb/5D0E6B108BAA4E0CAD1C559120C6123F1kernelbase.pdb
Loaded symbol image file: C:/Windows/System32/KERNELBASE.dll
Image path: C:/Windows/System32/KERNELBASE.dll
Image name: KERNELBASE.dll
Browse all global symbols functions data
Timestamp: Sat Jul 16 10:12:25 2016 (57899809)
CheckSum: 00221D33
ImageSize: 0021D000
File version: 10.0.14393.0
Product version: 10.0.14393.0
File flags: 0 (Mask 3F)
File OS: 40004 NT Win32
File type: 2.0 Dll
File date: 00000000.00000000
Translations: 0409.04b0
CompanyName: Microsoft Corporation
ProductName: Microsoft? Windows? Operating System
InternalName: Kernelbase.dll
OriginalFilename: Kernelbase.dll
ProductVersion: 10.0.14393.0
FileVersion: 10.0.14393.0 (rs1_release.160715-1616)
FileDescription: Windows NT BASE API Client DLL
LegalCopyright: ? Microsoft Corporation. All rights reserved.
```
- 加載符號文件。
```
0:000> .sympath
Symbol search path is: C:/Symbols
Expanded Symbol search path is: c:/symbols
************* Symbol Path validation summary **************
Response Time (ms) Location
OK C:/Symbols
0:000> .reload /f
Reloading current modules
.......................
0:000> lm
start end module name
00007ff6`c00a0000 00007ff6`c00ad000 calc (pdb symbols) c:/symbols/calc.pdb/BBD33747DAF54B2D9AD9F02861D972F81/calc.pdb
00007ffc`b02b0000 00007ffc`b02c4000 profapi (pdb symbols) c:/symbols/profapi.pdb/CAC4E3CC2E9B4973B17D131D0EFC8ACE1/profapi.pdb
00007ffc`b02e0000 00007ffc`b02ef000 kernel_appcore (pdb symbols) c:/symbols/Kernel.Appcore.pdb/C765CB33A55844379117C2F71220C8D71/Kernel.Appcore.pdb
00007ffc`b02f0000 00007ffc`b033c000 powrprof (pdb symbols) c:/symbols/powrprof.pdb/74B38765BC2D4D1B9E53834273CE9ABF1/powrprof.pdb
00007ffc`b0340000 00007ffc`b04c2000 gdi32full (pdb symbols) c:/symbols/gdi32full.pdb/9A1C5DBA389740BA8568049E4C0603491/gdi32full.pdb
00007ffc`b0530000 00007ffc`b0572000 cfgmgr32 (pdb symbols) c:/symbols/cfgmgr32.pdb/0C85585E81E54222A3065E20B6C913D41/cfgmgr32.pdb
00007ffc`b0580000 00007ffc`b0629000 shcore (pdb symbols) c:/symbols/shcore.pdb/1375C24C4D13484FB31C5B2E9E690F321/shcore.pdb
00007ffc`b0800000 00007ffc`b0eda000 windows_storage (pdb symbols) c:/symbols/Windows.Storage.pdb/FA91DDC596884A82AA032E2E9A652C4E1/Windows.Storage.pdb
00007ffc`b0f90000 00007ffc`b0fae000 win32u (pdb symbols) c:/symbols/win32u.pdb/CE777C7E22FC4E43A47A1D6EF5E1AF031/win32u.pdb
00007ffc`b0fb0000 00007ffc`b10a5000 ucrtbase (pdb symbols) c:/symbols/ucrtbase.pdb/5347FBF2D7FD4C99A15D54787482262A1/ucrtbase.pdb
00007ffc`b10b0000 00007ffc`b12cd000 KERNELBASE (pdb symbols) c:/symbols/kernelbase.pdb/5D0E6B108BAA4E0CAD1C559120C6123F1/kernelbase.pdb
...
```
- 單步步過、單步步入。查看反匯編代碼時,“.” 表示當(dāng)前運行的指令處,另外,在命令輸入時如果直接回車,則完成的操作和上一條命令相同。
```
0:000:x86> ub
KERNELBASE!LoadLibraryExW+0x23:
75a392b3 8b5d10 mov ebx,dword ptr [ebp+10h]
75a392b6 f7c30080ffff test ebx,0FFFF8000h
75a392bc 0f850a010000 jne KERNELBASE!LoadLibraryExW+0x13c (75a393cc)
75a392c2 8bf3 mov esi,ebx
75a392c4 83e642 and esi,42h
75a392c7 83fe42 cmp esi,42h
75a392ca 0f84fc000000 je KERNELBASE!LoadLibraryExW+0x13c (75a393cc)
75a392d0 50 push eax
0:000:x86> u .
KERNELBASE!LoadLibraryExW+0x41:
75a392d1 8d442424 lea eax,[esp+24h]
75a392d5 50 push eax
75a392d6 ff157081ae75 call dword ptr [KERNELBASE!WakeConditionVariable+0x4756 (75ae8170)]
75a392dc 85c0 test eax,eax
75a392de 0f8801ac0300 js KERNELBASE!GetCurrentProcess+0x8425 (75a73ee5)
75a392e4 668b4c2420 mov cx,word ptr [esp+20h]
75a392e9 8b542424 mov edx,dword ptr [esp+24h]
75a392ed 6685c9 test cx,cx
0:000:x86> p
KERNELBASE!LoadLibraryExW+0x45:
75a392d5 50 push eax
0:000:x86>
KERNELBASE!LoadLibraryExW+0x46:
75a392d6 ff157081ae75 call dword ptr [KERNELBASE!WakeConditionVariable+0x4756 (75ae8170)] ds:002b:75ae8170={ntdll_77820000!RtlInitUnicodeStringEx (77853380)}
0:000:x86> t
ntdll_77820000!RtlInitUnicodeStringEx:
77853380 8bff mov edi,edi
```
- 列舉函數(shù)名、設(shè)置斷點、查看寄存器和內(nèi)存、查看調(diào)用棧的信息。其中,“L+數(shù)字” 表示輸出數(shù)目,“*” 為通配符。
```
0:009> bc *
0:009> x KERNELBASE!LoadLibrary*
00000000`75a38c10 KERNELBASE!LoadLibraryExA (<no parameter info>)
00000000`75a39290 KERNELBASE!LoadLibraryExW (<no parameter info>)
00000000`75a3a2f0 KERNELBASE!LoadLibraryA (<no parameter info>)
00000000`75a3c590 KERNELBASE!LoadLibraryW (<no parameter info>)
0:009> bm KERNELBASE!LoadLibrary*
1: 00000000`75a38c10 @!"KERNELBASE!LoadLibraryExA"
2: 00000000`75a39290 @!"KERNELBASE!LoadLibraryExW"
3: 00000000`75a3a2f0 @!"KERNELBASE!LoadLibraryA"
4: 00000000`75a3c590 @!"KERNELBASE!LoadLibraryW"
0:009> bl
1 e x86 00000000`75a38c10 0001 (0001) 0:**** KERNELBASE!LoadLibraryExA
2 e x86 00000000`75a39290 0001 (0001) 0:**** KERNELBASE!LoadLibraryExW
3 e x86 00000000`75a3a2f0 0001 (0001) 0:**** KERNELBASE!LoadLibraryA
4 e x86 00000000`75a3c590 0001 (0001) 0:**** KERNELBASE!LoadLibraryW
0:009> bd 1 2
0:009> g
Breakpoint 3 hit
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:/Program Files (x86)/Common Files/Microsoft Shared/office14/riched20.dll -
KERNELBASE!LoadLibraryA:
75a3a2f0 8bff mov edi,edi
0:000:x86> r
eax=00000000 ebx=00000000 ecx=00bdc355 edx=6fd20950 esi=6fd20890 edi=00000000
eip=75a3a2f0 esp=00bdc3b4 ebp=00bdc40c iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
KERNELBASE!LoadLibraryA:
75a3a2f0 8bff mov edi,edi
0:000:x86> dd esp L4
00bdc3b4 6fc0d839 6fd20950 000000cc 097d05c8
0:000:x86> da poi(esp+4)
6fd20950 "UxTheme.dll"
0:000:x86> bd *
0:000:x86> bp KERNELBASE!LoadLibraryA ".if(ebx=0){}.else{gc}"
breakpoint 3 redefined
0:000:x86> g
KERNELBASE!LoadLibraryA:
75a3a2f0 8bff mov edi,edi
0:000:x86> r
eax=00000000 ebx=00000000 ecx=00bdc649 edx=6fd20930 esi=6fd20850 edi=00000000
eip=75a3a2f0 esp=00bdc6a0 ebp=00bdc6f8 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
KERNELBASE!LoadLibraryA:
75a3a2f0 8bff mov edi,edi
0:000:x86> k L5
# ChildEBP RetAddr
WARNING: Stack unwind information not available. Following frames may be wrong.
00 00bdc69c 6fc0d839 KERNELBASE!LoadLibraryA
01 00bdc6f8 6fc1f79f riched20!IID_ITextServices2+0x3b09
02 00bdc718 6fc7e13f riched20!RichListBoxWndProc+0x13a8
03 00bdc738 6fc0a3b7 riched20!IID_ITextHost2+0x3672f
04 00bdc754 6fc09f8d riched20!IID_ITextServices2+0x687
```
- 條件斷點與硬件斷點,設(shè)置斷點時可通過`.echo`命令打印一些日志信息。
```
0:004> bp KERNELBASE!LoadLibraryA ".echo 'Hi, this is a LoadLibraryA break!'"
0:004> bl
0 e 00007ffa`7635b680 0001 (0001) 0:**** KERNELBASE!LoadLibraryA ".echo 'Hi, this is a LoadLibraryA break!'"
0:004> g
ModLoad: 00007ffa`71f40000 00007ffa`71f76000 C:Windowssystem32xmllite.dll
'Hi, this is a LoadLibraryA break!'
KERNELBASE!LoadLibraryA:
00007ffa`7635b680 48895c2408 mov qword ptr [rsp+8],rbx ss:000000dc`4db7f810=000000008004000a
...
0:000> bp KERNELBASE!LoadLibraryExW ".if(rax > 0xff){.echo 'rax > 0xff'}.else{.echo 'rax <= 0xff'; gc}"
0:000> bl
0 e 00007ffa`7631c8b0 0001 (0001) 0:**** KERNELBASE!LoadLibraryExW ".if(rax > 0xff){.echo 'rax > 0xff'}.else{.echo 'rax <= 0xff'; gc}"
0:000> g
'rax > 0xff'
KERNELBASE!LoadLibraryExW:
00007ffa`7631c8b0 4055 push rbp
0:000> g
ModLoad: 00007ffa`78460000 00007ffa`7848e000 C:WindowsSystem32IMM32.DLL
'rax <= 0xff'
'rax <= 0xff'
'rax <= 0xff'
'rax <= 0xff'
'rax <= 0xff'
'rax <= 0xff'
'rax <= 0xff'
ModLoad: 00007ffa`73d80000 00007ffa`73e15000 C:Windowssystem32uxtheme.dll
ModLoad: 00007ffa`76720000 00007ffa`7687b000 C:WindowsSystem32MSCTF.dll
ModLoad: 00007ffa`73a30000 00007ffa`73a56000 C:Windowssystem32dwmapi.dll
ModLoad: 00007ffa`78e70000 00007ffa`78f0f000 C:WindowsSystem32clbcatq.dll
'rax > 0xff'
KERNELBASE!LoadLibraryExW:
00007ffa`7631c8b0 4055 push rbp
0:000> r rax
rax=000000a0107cdf78
0:000> bc *
0:000> ba e1 00007ffa`7631c8b0
0:000> bl
0 e 00007ffa`7631c8b0 e 1 0001 (0001) 0:**** KERNELBASE!LoadLibraryExW
0:000> g
Breakpoint 0 hit
KERNELBASE!LoadLibraryExW:
00007ffa`7631c8b0 4055 push rbp
```
- 查看特定函數(shù)的反匯編代碼。
```
0:001> uf KERNELBASE!LoadLibraryA
Flow analysis was incomplete, some code may be missing
KERNELBASE!LoadLibraryA:
00000000`75a3a2f0 8bff mov edi,edi
00000000`75a3a2f2 55 push rbp
00000000`75a3a2f3 8bec mov ebp,esp
00000000`75a3a2f5 51 push rcx
00000000`75a3a2f6 837d0800 cmp dword ptr [rbp+8],0
00000000`75a3a2fa 53 push rbx
00000000`75a3a2fb 56 push rsi
00000000`75a3a2fc 7418 je KERNELBASE!LoadLibraryA+0x26 (00000000`75a3a316) Branch
KERNELBASE!LoadLibraryA+0xe:
00000000`75a3a2fe 68d0129b75 push offset KERNELBASE+0x412d0 (00000000`759b12d0)
00000000`75a3a303 ff7508 push qword ptr [rbp+8]
00000000`75a3a306 ff155886ae75 call qword ptr [00000000`eb522964]
...
```
- 查看內(nèi)存堆信息、搜索內(nèi)存。
```
0:005> !heap -h
Index Address Name Debugging options enabled
1: 2d1990b0000
Segment at 000002d1990b0000 to 000002d1991af000 (00056000 bytes committed)
2: 2d198ff0000
Segment at 000002d198ff0000 to 000002d199000000 (00001000 bytes committed)
3: 2d1993c0000
Segment at 000002d1993c0000 to 000002d1993cf000 (00007000 bytes committed)
4: 2d199390000
Segment at 000002d199390000 to 000002d19939f000 (00009000 bytes committed)
0:005> !heap -p -a 2d1990b1000
address 000002d1990b1000 found in
_HEAP @ 2d1990b0000
HEAP_ENTRY Size Prev Flags UserPtr UserSize - state
000002d1990b0ef0 00ca 0000 [00] 000002d1990b0f00 00c6c - (busy)
0:005> s -sa 2d1990b0000 L4000
000002d1`990b0736 "-3E"
000002d1`990b08e2 "_0*"
000002d1`990b08ea "`"0"
000002d1`990b243f "0@+"
000002d1`990b260f "0@$"
000002d1`990b3128 "PZm4"
000002d1`990b340f "0C:/Windows/System32/notepad.exe"
000002d1`990b3e11 "up4"
0:005> s -a 2d1990b0000 L4000 "notepad"
000002d1`990b3424 6e 6f 74 65 70 61 64 2e-65 78 65 00 ab ab ab ab notepad.exe.....
```
- 查看相關(guān)的符號信息。
```
0:000> dqs rsp
000000ad`0152f5e0 00000000`00000000
000000ad`0152f5e8 000000ad`0152f670
000000ad`0152f5f0 00000000`00000000
000000ad`0152f5f8 000000ad`0152f670
000000ad`0152f600 00000000`00000000
000000ad`0152f608 00007ffc`b3ebe0c0 ntdll!`string'
000000ad`0152f610 000000ad`017dc000
000000ad`0152f618 00007ffc`b3e41b92 ntdll!LdrpInitializeProcess+0x1962
000000ad`0152f620 00000000`00000000
000000ad`0152f628 00000000`00000003
000000ad`0152f630 00000000`00000003
000000ad`0152f638 00000000`00000003
000000ad`0152f640 00000000`00000000
000000ad`0152f648 000000ad`0152f900
000000ad`0152f650 00000000`00000000
000000ad`0152f658 00000000`00000000
0:000> kb
# RetAddr : Args to Child : Call Site
00 00007ffc`b3e41b92 : 00000000`00000000 00000000`00000003 00000000`00000003 00000000`00000003 : ntdll!LdrpDoDebuggerBreak+0x30
01 00007ffc`b3e77af4 : 00000000`00000000 00007ffc`b3e38bc9 00000000`00000000 00000000`00000001 : ntdll!LdrpInitializeProcess+0x1962
02 00007ffc`b3e28d5e : 000000ad`0152faf0 00000000`00000000 00000000`00000000 000000ad`017dc000 : ntdll!_LdrpInitialize+0x4ed40
03 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ntdll!LdrInitializeThunk+0xe
0:000> ln 00007ffc`b3e38bc9
Browse module
Set bu breakpoint
(00007ffc`b3e38b88) ntdll!InitSecurityCookie+0x41 | (00007ffc`b3e38bf0) ntdll!RtlDoesFileExists_U
```
- `?`在運算時還是很有用的,其中,“0x” 表示 16 進制、“0n” 表示 10 進制、“0t” 表示 8 進制、“0y” 表示 2 進制,默認情況是 16 進制。
```
0:004> ? 0x100
Evaluate expression: 256 = 00000000`00000100
0:004> ? 0n100
Evaluate expression: 100 = 00000000`00000064
0:004> ? 0t100
Evaluate expression: 64 = 00000000`00000040
0:004> ? 0y100
Evaluate expression: 4 = 00000000`00000004
0:004> ? 100
Evaluate expression: 256 = 00000000`00000100
0:004> ? 0x100+0n100
Evaluate expression: 356 = 00000000`00000164
0:004> qd
```
**ring0 常見命令及使用技巧**
這里用到雙虛擬機調(diào)試環(huán)境,具體配置可參照[此文](https://ephrain.net/windbg-%E5%9C%A8-mac-virtualbox%E4%B8%8A%E8%A8%AD%E5%AE%9A-windows-kernel-debugging-%E7%92%B0%E5%A2%83/),連接建立后會顯示如下信息:
```
Microsoft (R) Windows Debugger Version 10.0.14321.1024 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Opened .com1
Waiting to reconnect...
Connected to Windows 10 14393 x64 target at (Tue Dec 19 15:55:49.108 2017 (UTC + 8:00)), ptr64 TRUE
Kernel Debugger connection established.
************* Symbol Path validation summary **************
Response Time (ms) Location
OK C:/Symbols
Symbol search path is: C:/Symbols
Executable search path is:
Windows 10 Kernel Version 14393 MP (1 procs) Free x64
Built by: 14393.0.amd64fre.rs1_release.160715-1616
Machine Name:
Kernel base = 0xfffff800`af419000 PsLoadedModuleList = 0xfffff800`af71e060
System Uptime: 0 days 0:00:00.025
KDTARGET: Refreshing KD connection
```
說明一點,前面介紹的 ring3 層調(diào)試命令大多在 ring0 層也是適用的,同樣,接下去介紹的有些命令也適用于 ring3 層,我們繼續(xù):
- 查看進程列表、進程中的線程、切換進程上下文。
```
kd> !process 0 0
**** NT ACTIVE PROCESS DUMP ****
PROCESS ffffb98dd065a040
SessionId: none Cid: 0004 Peb: 00000000 ParentCid: 0000
DirBase: 001aa000 ObjectTable: ffff9e0212001340 HandleCount: <Data Not Accessible>
Image: System
PROCESS ffffb98dd18fd040
SessionId: none Cid: 0118 Peb: 63d31d1000 ParentCid: 0004
DirBase: 7be6d000 ObjectTable: ffff9e02125e9280 HandleCount: <Data Not Accessible>
Image: smss.exe
PROCESS ffffb98dd1c01780
SessionId: 0 Cid: 0168 Peb: ccec47a000 ParentCid: 0160
DirBase: 0c0c1000 ObjectTable: ffff9e0212132a80 HandleCount: <Data Not Accessible>
Image: csrss.exe
PROCESS ffffb98dd21de080
SessionId: 1 Cid: 019c Peb: ab7b3d9000 ParentCid: 0118
DirBase: 0e0c1000 ObjectTable: 00000000 HandleCount: 0.
Image: smss.exe
...
PROCESS ffffb98dd251b080
SessionId: 1 Cid: 0290 Peb: 68a6eb3000 ParentCid: 09d8
DirBase: 0fcaa000 ObjectTable: ffff9e0219d2dc40 HandleCount: <Data Not Accessible>
Image: notepad.exe
kd> !process ffffb98dd251b080 2
PROCESS ffffb98dd251b080
SessionId: 1 Cid: 0290 Peb: 68a6eb3000 ParentCid: 09d8
DirBase: 0fcaa000 ObjectTable: ffff9e0219d2dc40 HandleCount: <Data Not Accessible>
Image: notepad.exe
THREAD ffffb98dd2cd9080 Cid 0290.0370 Teb: 00000068a6eb4000 Win32Thread: ffffb98dd1068820 WAIT: (WrUserRequest) UserMode Non-Alertable
ffffb98dd2d11de0 SynchronizationEvent
THREAD ffffb98dd254f080 Cid 0290.0844 Teb: 00000068a6eb6000 Win32Thread: 0000000000000000 WAIT: (WrQueue) UserMode Alertable
ffffb98dd2238e80 QueueObject
THREAD ffffb98dd108b080 Cid 0290.0854 Teb: 00000068a6eb8000 Win32Thread: 0000000000000000 WAIT: (WrQueue) UserMode Alertable
ffffb98dd2e5f540 QueueObject
THREAD ffffb98dd2572080 Cid 0290.08e0 Teb: 00000068a6eba000 Win32Thread: 0000000000000000 WAIT: (WrQueue) UserMode Alertable
ffffb98dd2e5f540 QueueObject
...
kd> .process
Implicit process is now ffffb98d`d065a040
kd> .process /i /p ffffb98dd251b080
You need to continue execution (press 'g' <enter>) for the context
to be switched. When the debugger breaks in again, you will be in
the new process context.
kd> g
Break instruction exception - code 80000003 (first chance)
nt!DbgBreakPointWithStatus:
fffff800`af568a60 cc int 3
kd> .process
Implicit process is now ffffb98d`d251b080
```
- 查看結(jié)構(gòu)體的類型定義。
```
kd> dt nt!_PEB
dtx is unsupported for this scenario. It only recognizes dtx [<type>] [<address>] with -a, -h, and -r. Reverting to dt.
+0x000 InheritedAddressSpace : UChar
+0x001 ReadImageFileExecOptions : UChar
+0x002 BeingDebugged : UChar
+0x003 BitField : UChar
+0x003 ImageUsesLargePages : Pos 0, 1 Bit
+0x003 IsProtectedProcess : Pos 1, 1 Bit
+0x003 IsImageDynamicallyRelocated : Pos 2, 1 Bit
+0x003 SkipPatchingUser32Forwarders : Pos 3, 1 Bit
+0x003 IsPackagedProcess : Pos 4, 1 Bit
+0x003 IsAppContainer : Pos 5, 1 Bit
+0x003 IsProtectedProcessLight : Pos 6, 1 Bit
+0x003 IsLongPathAwareProcess : Pos 7, 1 Bit
+0x004 Padding0 : [4] UChar
+0x008 Mutant : Ptr64 Void
+0x010 ImageBaseAddress : Ptr64 Void
...
```
參考:
[1] Windbg調(diào)試命令詳解
[http://www.yiiyee.cn/Blog/windbg/](http://www.yiiyee.cn/Blog/windbg/)
[2] Getting Started with Windows Debugging
[https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/getting-started-with-windows-debugging](https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/getting-started-with-windows-debugging)
?
問答
其他問答

暫無記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開":"未公開"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無記錄
作業(yè)

暫無記錄

